Email is one of the most commonly used communication channels—and one of the most frequently abused. Cybercriminals exploit email to spoof identities, phish users, and spread malware. To combat this, email authentication protocols like SPF, DKIM, and DMARC work together to protect domain owners and recipients from fraudulent email activity. Let’s break down how each protocol works, what the possible results mean, and how they reinforce one another to secure your email infrastructure.
1. SPF (Sender Policy Framework)
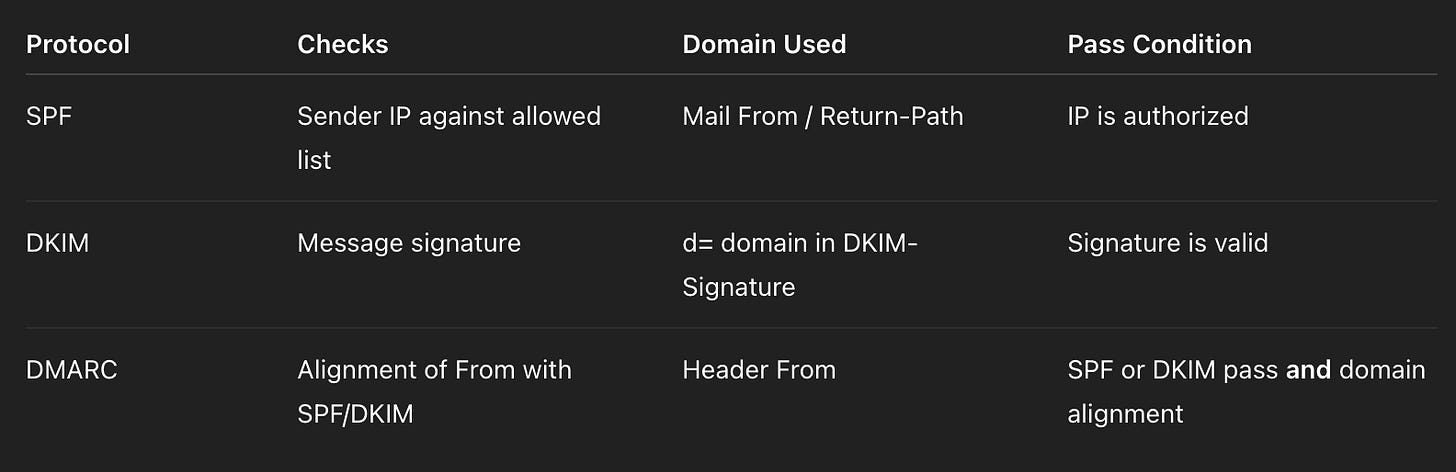
Purpose: Prevents unauthorized servers from sending emails on behalf of your domain.
How It Works: SPF checks the Mail From domain (also called the "envelope from") against a list of IP addresses authorized to send on behalf of that domain, as defined in your domain’s DNS.
Example SPF record:
v=spf1 include:_spf.google.com ~allThis record says: only Google’s servers are allowed to send email for this domain.
SPF Results (in Authentication Headers):
Pass: The sending IP is listed in the SPF record.None: No SPF record found.Neutral: SPF is not explicitly allowing or disallowing the sender.SoftFail: The sender is not authorized, but the failure is not strict (often marked as suspicious).Fail: The sender is not authorized and the policy is strict—treat as spam or reject.
You’ll see this in headers like:
Received-SPF: pass (google.com: domain of sender@domain.com designates x.x.x.x as permitted sender)
Authentication-Results: spf=pass2. DKIM (DomainKeys Identified Mail)
Purpose: Ensures the content of an email hasn’t been tampered with and verifies it was sent by an authorized domain.
How It Works: The sender's server signs specific parts of the email using a private cryptographic key. The receiving server retrieves the public key from DNS to validate the signature. This uses the DKIM From domain (a.k.a. d= domain).
Example DKIM record:
v=DKIM1; k=rsa; p=MIIBIjANBgkqh...DKIM Results:
Pass: Signature is valid and verified.None: No DKIM signature found.Fail: Signature doesn’t match or can’t be verified.
In the email header:
Authentication-Results: dkim=pass (signature verified) header.d=yourdomain.com3. DMARC (Domain-based Message Authentication, Reporting, and Conformance)
Purpose: Aligns SPF and DKIM results with the domain in the From header and tells receiving servers how to handle failures.
How It Works: DMARC policies are published in DNS and specify:
Whether to monitor, quarantine, or reject messages that fail SPF or DKIM.
Where to send aggregate and forensic reports (via
ruaorruftags).
Example DMARC record:
v=DMARC1; p=reject; rua=mailto:reports@yourdomain.comp=reject: Block emails that fail authentication.rua=mailto:reports@yourdomain.com: Send daily reports to this address.
DMARC Pass Conditions:
At least SPF or DKIM must pass, and the passing method must align with the From header domain.
How SPF, DKIM, and DMARC Work Together
Example DMARC alignment:
SPF From = Mail From
DKIM From = d= domain in signature
To pass DMARC, either SPF or DKIM (or both) must pass and their domains must match the visible "From" address in the email.
Conclusion
Implementing SPF, DKIM, and DMARC ensures your domain cannot be impersonated by malicious actors. Together, they:
Authenticate the source and integrity of your email
Help receiving servers recognize legitimate messages
Reduce the risk of spoofing, phishing, and spam
Every organization that sends email should implement and monitor these records to protect their reputation, customers, and partners. Don’t wait until your domain is spoofed—secure your email today.