Understanding TLS Handshake Message Types in Wireshark
Wireshark is a powerful network protocol analyzer that provides deep visibility into network traffic. One of its most valuable features is the ability to inspect Transport Layer Security (TLS) handshakes — the process through which secure communication is established between clients and servers.
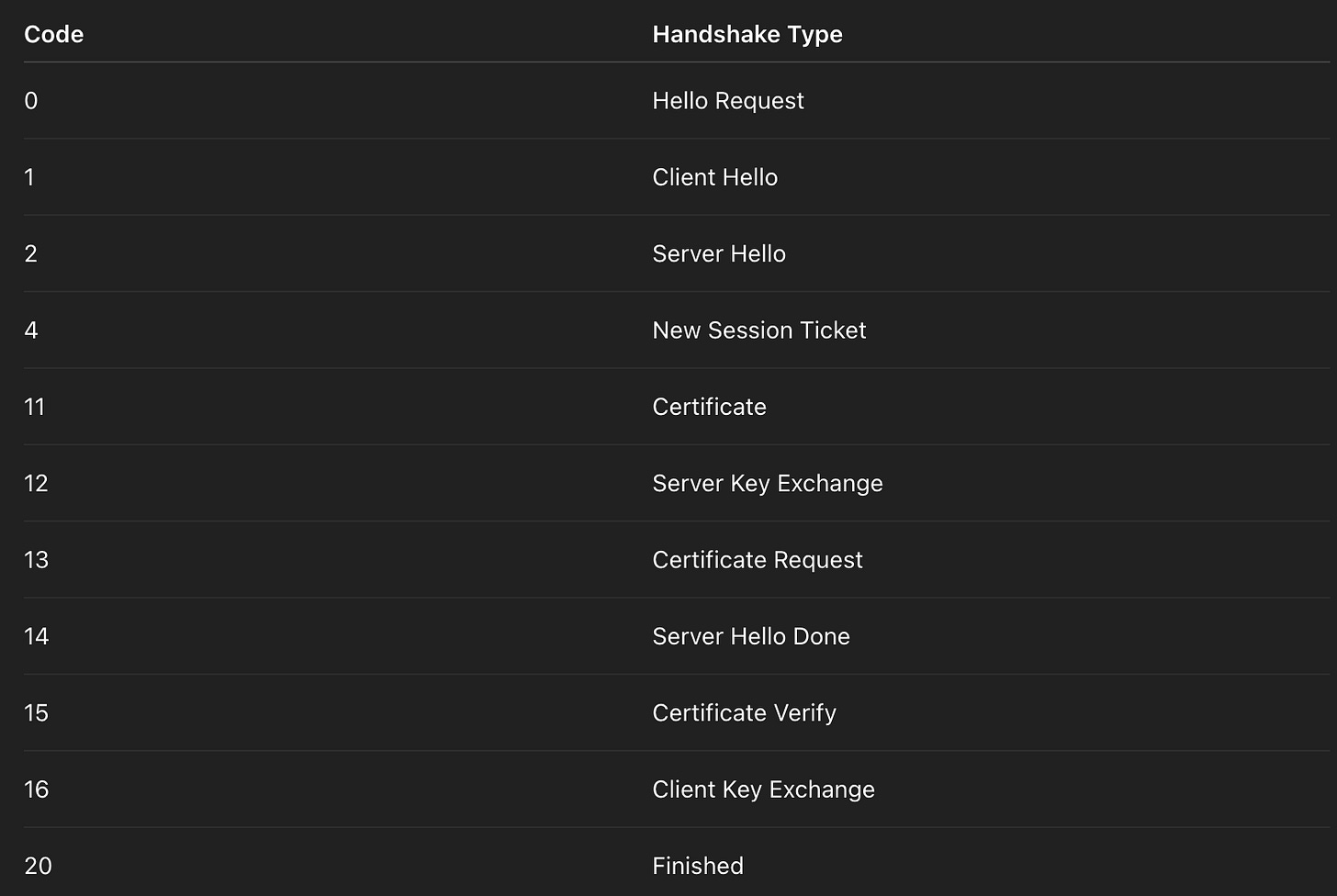
Each step of the TLS handshake is represented by a specific message type, and Wireshark identifies these using the tls.handshake.type field. Understanding these message types can help security professionals, developers, and network administrators diagnose SSL/TLS-related issues, detect anomalies, or simply learn how secure connections are established.
TLS Handshake Types and Their Codes
In Wireshark, the tls.handshake.type field corresponds to different handshake message types. Below is a table showing the most common TLS handshake messages and their respective numerical codes:
These messages work together to:
Negotiate security parameters
Authenticate parties
Perform key exchange
Establish a secure session
For instance, the Client Hello (code 1) and Server Hello (code 2) messages are used to initiate and negotiate the TLS session. The Certificate (code 11) message is used by the server to provide its identity to the client. Finally, the Finished (code 20) message marks the end of the handshake and the beginning of secure communication.
Filtering TLS Handshake Messages in Wireshark
Wireshark allows you to apply filters to inspect specific parts of network traffic. To view a specific TLS handshake message, use the following filter syntax:
tls.handshake.type == <code>Examples:
Client Hello messages:
tls.handshake.type == 1Server Hello messages:
tls.handshake.type == 2Certificate messages:
tls.handshake.type == 11Client Key Exchange messages:
tls.handshake.type == 16You can also filter for multiple types using logical OR (||) operators:
tls.handshake.type == 1 || tls.handshake.type == 2This would show both Client Hello and Server Hello messages.
Why It Matters
Inspecting TLS handshake messages in Wireshark can help you:
Debug SSL/TLS configuration errors
Verify certificate exchange and validation
Identify outdated or insecure protocol versions
Understand connection timing and negotiation behavior
Whether you're troubleshooting a failed HTTPS connection or ensuring compliance with security policies, knowing how to interpret and filter TLS handshake messages is a critical skill.
Conclusion
The tls.handshake.type field in Wireshark provides a powerful way to explore the step-by-step negotiation of a secure TLS session. By understanding the different message types and how to filter them, you can gain deep insights into your network's encrypted communications.